介绍
Kiali 的官方文档:https://kiali.io/docs/installation/quick-start/
Kiali 是具有服务网格配置和验证功能的 Istio 可观察性的控制台。通过监视流量来推断拓扑和错误报告,它可以帮助您了解服务网格的结构和运行状态。 Kiali 提供了详细的的指标并与 Grafana 进行基础集成,可以用于高级查询。通过与 Jaeger 来提供分布式链路追踪功能。
部署
这里使用istio的快速部署
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.18/samples/addons/kiali.yaml---
# Source: kiali-server/templates/serviceaccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: kiali
namespace: istio-system
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
---
# Source: kiali-server/templates/configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: kiali
namespace: istio-system
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
data:
config.yaml: |
auth:
openid: {}
openshift:
client_id_prefix: kiali
strategy: anonymous
deployment:
accessible_namespaces:
- '**'
additional_service_yaml: {}
affinity:
node: {}
pod: {}
pod_anti: {}
configmap_annotations: {}
custom_secrets: []
host_aliases: []
hpa:
api_version: autoscaling/v2beta2
spec: {}
image_digest: ""
image_name: quay.io/kiali/kiali
image_pull_policy: Always
image_pull_secrets: []
image_version: v1.67
ingress:
additional_labels: {}
class_name: nginx
override_yaml:
metadata: {}
ingress_enabled: false
instance_name: kiali
logger:
log_format: text
log_level: info
sampler_rate: "1"
time_field_format: 2006-01-02T15:04:05Z07:00
namespace: istio-system
node_selector: {}
pod_annotations: {}
pod_labels:
sidecar.istio.io/inject: "false"
priority_class_name: ""
replicas: 1
resources:
limits:
memory: 1Gi
requests:
cpu: 10m
memory: 64Mi
secret_name: kiali
security_context: {}
service_annotations: {}
service_type: ""
tolerations: []
version_label: v1.67.0
view_only_mode: false
external_services:
custom_dashboards:
enabled: true
istio:
root_namespace: istio-system
identity:
cert_file: ""
private_key_file: ""
istio_namespace: istio-system
kiali_feature_flags:
certificates_information_indicators:
enabled: true
secrets:
- cacerts
- istio-ca-secret
clustering:
autodetect_secrets:
enabled: true
label: kiali.io/multiCluster=true
clusters: []
disabled_features: []
validations:
ignore:
- KIA1201
login_token:
signing_key: CHANGEME00000000
server:
metrics_enabled: true
metrics_port: 9090
port: 20001
web_root: /kiali
---
# Source: kiali-server/templates/role-viewer.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: kiali-viewer
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
rules:
- apiGroups: [""]
resources:
- configmaps
- endpoints
- pods/log
verbs:
- get
- list
- watch
- apiGroups: [""]
resources:
- namespaces
- pods
- replicationcontrollers
- services
verbs:
- get
- list
- watch
- apiGroups: [""]
resources:
- pods/portforward
verbs:
- create
- post
- apiGroups: ["extensions", "apps"]
resources:
- daemonsets
- deployments
- replicasets
- statefulsets
verbs:
- get
- list
- watch
- apiGroups: ["batch"]
resources:
- cronjobs
- jobs
verbs:
- get
- list
- watch
- apiGroups:
- networking.istio.io
- security.istio.io
- extensions.istio.io
- telemetry.istio.io
- gateway.networking.k8s.io
resources: ["*"]
verbs:
- get
- list
- watch
- apiGroups: ["apps.openshift.io"]
resources:
- deploymentconfigs
verbs:
- get
- list
- watch
- apiGroups: ["project.openshift.io"]
resources:
- projects
verbs:
- get
- apiGroups: ["route.openshift.io"]
resources:
- routes
verbs:
- get
- apiGroups: ["authentication.k8s.io"]
resources:
- tokenreviews
verbs:
- create
---
# Source: kiali-server/templates/role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: kiali
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
rules:
- apiGroups: [""]
resources:
- configmaps
- endpoints
- pods/log
verbs:
- get
- list
- watch
- apiGroups: [""]
resources:
- namespaces
- pods
- replicationcontrollers
- services
verbs:
- get
- list
- watch
- patch
- apiGroups: [""]
resources:
- pods/portforward
verbs:
- create
- post
- apiGroups: ["extensions", "apps"]
resources:
- daemonsets
- deployments
- replicasets
- statefulsets
verbs:
- get
- list
- watch
- patch
- apiGroups: ["batch"]
resources:
- cronjobs
- jobs
verbs:
- get
- list
- watch
- patch
- apiGroups:
- networking.istio.io
- security.istio.io
- extensions.istio.io
- telemetry.istio.io
- gateway.networking.k8s.io
resources: ["*"]
verbs:
- get
- list
- watch
- create
- delete
- patch
- apiGroups: ["apps.openshift.io"]
resources:
- deploymentconfigs
verbs:
- get
- list
- watch
- patch
- apiGroups: ["project.openshift.io"]
resources:
- projects
verbs:
- get
- apiGroups: ["route.openshift.io"]
resources:
- routes
verbs:
- get
- apiGroups: ["authentication.k8s.io"]
resources:
- tokenreviews
verbs:
- create
---
# Source: kiali-server/templates/rolebinding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kiali
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kiali
subjects:
- kind: ServiceAccount
name: kiali
namespace: istio-system
---
# Source: kiali-server/templates/role-controlplane.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: kiali-controlplane
namespace: istio-system
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
rules:
- apiGroups: [""]
resourceNames:
- cacerts
- istio-ca-secret
resources:
- secrets
verbs:
- get
- list
- watch
---
# Source: kiali-server/templates/rolebinding-controlplane.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kiali-controlplane
namespace: istio-system
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kiali-controlplane
subjects:
- kind: ServiceAccount
name: kiali
namespace: istio-system
---
# Source: kiali-server/templates/service.yaml
apiVersion: v1
kind: Service
metadata:
name: kiali
namespace: istio-system
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
annotations:
spec:
ports:
- name: http
appProtocol: http
protocol: TCP
port: 20001
- name: http-metrics
appProtocol: http
protocol: TCP
port: 9090
selector:
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
---
# Source: kiali-server/templates/deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: kiali
namespace: istio-system
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
spec:
replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
strategy:
rollingUpdate:
maxSurge: 1
maxUnavailable: 1
type: RollingUpdate
template:
metadata:
name: kiali
labels:
helm.sh/chart: kiali-server-1.67.0
app: kiali
app.kubernetes.io/name: kiali
app.kubernetes.io/instance: kiali
version: "v1.67.0"
app.kubernetes.io/version: "v1.67.0"
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/part-of: "kiali"
sidecar.istio.io/inject: "false"
annotations:
checksum/config: 88419f205248a3fdba75ba592ce095a39000318ed6056baaa08ea19d716e94c1
prometheus.io/scrape: "true"
prometheus.io/port: "9090"
kiali.io/dashboards: go,kiali
spec:
serviceAccountName: kiali
containers:
- image: "quay.io/kiali/kiali:v1.67"
imagePullPolicy: Always
name: kiali
command:
- "/opt/kiali/kiali"
- "-config"
- "/kiali-configuration/config.yaml"
securityContext:
allowPrivilegeEscalation: false
privileged: false
readOnlyRootFilesystem: true
runAsNonRoot: true
capabilities:
drop:
- ALL
ports:
- name: api-port
containerPort: 20001
- name: http-metrics
containerPort: 9090
readinessProbe:
httpGet:
path: /kiali/healthz
port: api-port
scheme: HTTP
initialDelaySeconds: 5
periodSeconds: 30
livenessProbe:
httpGet:
path: /kiali/healthz
port: api-port
scheme: HTTP
initialDelaySeconds: 5
periodSeconds: 30
env:
- name: ACTIVE_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LOG_LEVEL
value: "info"
- name: LOG_FORMAT
value: "text"
- name: LOG_TIME_FIELD_FORMAT
value: "2006-01-02T15:04:05Z07:00"
- name: LOG_SAMPLER_RATE
value: "1"
volumeMounts:
- name: kiali-configuration
mountPath: "/kiali-configuration"
- name: kiali-cert
mountPath: "/kiali-cert"
- name: kiali-secret
mountPath: "/kiali-secret"
- name: kiali-cabundle
mountPath: "/kiali-cabundle"
resources:
limits:
memory: 1Gi
requests:
cpu: 10m
memory: 64Mi
volumes:
- name: kiali-configuration
configMap:
name: kiali
- name: kiali-cert
secret:
secretName: istio.kiali-service-account
optional: true
- name: kiali-secret
secret:
secretName: kiali
optional: true
- name: kiali-cabundle
configMap:
name: kiali-cabundle
optional: true
访问UI
修改svc为NodePort。登录后立即显示的 Overview 页面中查看网格的概述。Overview 页面显示了网格中具有服务的所有命名空间。
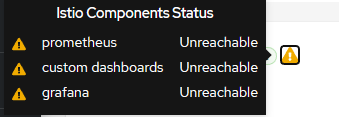
会报错,因为没有部署prometheus和grafana,custorm dashboard。

查看graph,报错无法loaload,因为prometheus没有部署。需要先部署。

安装遥测组件
部署服务
远程访问遥测插件的方式有很多种。安全的(通过 HTTPS)和不安全的(通过 HTTP)。 对于任何生产或敏感环境,强烈建议 通过安全方式访问。 不安全访问易于设置,但是无法保护在集群外传输的任何凭据或数据。
我这里本地环境就直接使用了HTTP。
安装命令:
Grafana: --set values.grafana.enabled=true
Kiali: --set values.kiali.enabled=true
Prometheus: --set values.prometheus.enabled=true
Tracing: --set values.tracing.enabled=true
# 有多种安装方式,我是用istioctl安装的控制平面,不是helm:
istioctl install --set profile=demo --set values.grafana.enabled=true --set values.grafana.enabled=true --set values.prometheus.enabled=true --set values.tracing.enabled=true
istioctl manifest generate --set profile=demo --set grafana.enabled=trueistioctl manifest generate --set profile=demo --set values.grafana.enabled=true --set values.kiali.enabled=true --set values.prometheus.enabled=true --set values.tracing.enabled=true > manifest.yaml
kubectl apply -f manifest.yaml
istioctl manifest apply --set values.grafana.enabled=true --set values.kiali.enabled=true --set values.prometheus.enabled=true --set values.tracing.enabled=true
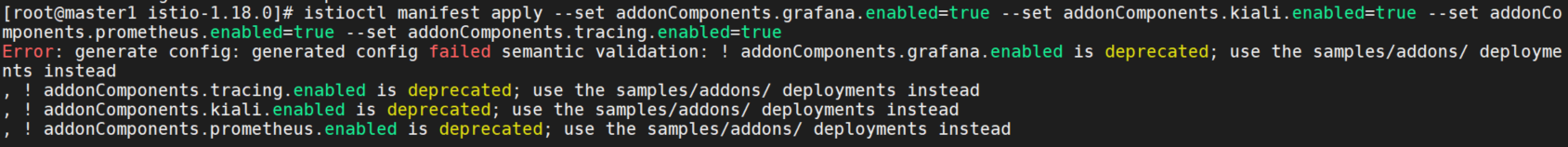
istioctl manifest apply --set addonComponents.grafana.enabled=true --set addonComponents.kiali.enabled=true --set addonComponents.prometheus.enabled=true --set addonComponents.tracing.enabled=true但是每一种我都试过了,都无法安装,报错:Error: generate config: unknown field "grafana" in v1alpha1.Values
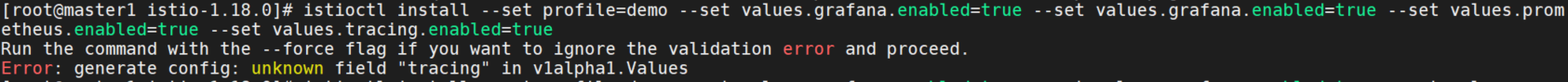
使用addonComponents这个参数时,提示该参数已经被取代了,需要使用use the samples/addons/ deployments instead
所以这里直接使用samples/addons/目录下的yaml来安装。
kubectl apply -f samples/addons/grafana.yaml
kubectl apply -f samples/addons/prometheus.yaml
kubectl apply -f samples/addons/loki.yaml -n istio-system(可选)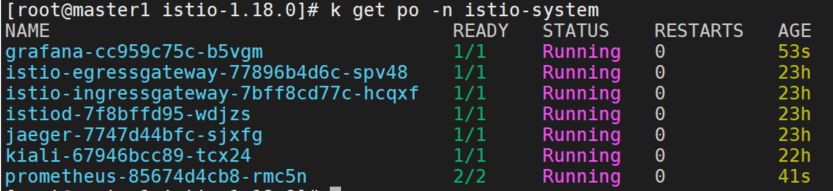
部署网关
前面修改了svc为NodePort,这是一种访问方式,也可以通过istio的ingress-gateway,部署网关,VirtualService,DestinationRule来实现。
grafana
cat <<EOF | kubectl apply -f -
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: grafana-gateway
namespace: istio-system
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 15031
name: http-grafana
protocol: HTTP
hosts:
- "*"
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: grafana-vs
namespace: istio-system
spec:
hosts:
- "*"
gateways:
- grafana-gateway
http:
- match:
- port: 15031
route:
- destination:
host: grafana
port:
number: 3000
---
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: grafana
namespace: istio-system
spec:
host: grafana
trafficPolicy:
tls:
mode: DISABLE
---
EOF
gateway.networking.istio.io "grafana-gateway" configured
virtualservice.networking.istio.io "grafana-vs" configured
destinationrule.networking.istio.io "grafana" configuredKiali
cat <<EOF | kubectl apply -f -
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: kiali-gateway
namespace: istio-system
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 15029
name: http-kiali
protocol: HTTP
hosts:
- "*"
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: kiali-vs
namespace: istio-system
spec:
hosts:
- "*"
gateways:
- kiali-gateway
http:
- match:
- port: 15029
route:
- destination:
host: kiali
port:
number: 20001
---
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: kiali
namespace: istio-system
spec:
host: kiali
trafficPolicy:
tls:
mode: DISABLE
---
EOF
gateway.networking.istio.io "kiali-gateway" configured
virtualservice.networking.istio.io "kiali-vs" configured
destinationrule.networking.istio.io "kiali" configuredPrometheus
cat <<EOF | kubectl apply -f -
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: prometheus-gateway
namespace: istio-system
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 15030
name: http-prom
protocol: HTTP
hosts:
- "*"
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: prometheus-vs
namespace: istio-system
spec:
hosts:
- "*"
gateways:
- prometheus-gateway
http:
- match:
- port: 15030
route:
- destination:
host: prometheus
port:
number: 9090
---
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: prometheus
namespace: istio-system
spec:
host: prometheus
trafficPolicy:
tls:
mode: DISABLE
---
EOF
gateway.networking.istio.io "prometheus-gateway" configured
virtualservice.networking.istio.io "prometheus-vs" configured
destinationrule.networking.istio.io "prometheus" configuredtracing
cat <<EOF | kubectl apply -f -
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: tracing-gateway
namespace: istio-system
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 15032
name: http-tracing
protocol: HTTP
hosts:
- "*"
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: tracing-vs
namespace: istio-system
spec:
hosts:
- "*"
gateways:
- tracing-gateway
http:
- match:
- port: 15032
route:
- destination:
host: tracing
port:
number: 80
---
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: tracing
namespace: istio-system
spec:
host: tracing
trafficPolicy:
tls:
mode: DISABLE
---
EOF
gateway.networking.istio.io "tracing-gateway" configured
virtualservice.networking.istio.io "tracing-vs" configured
destinationrule.networking.istio.io "tracing" configured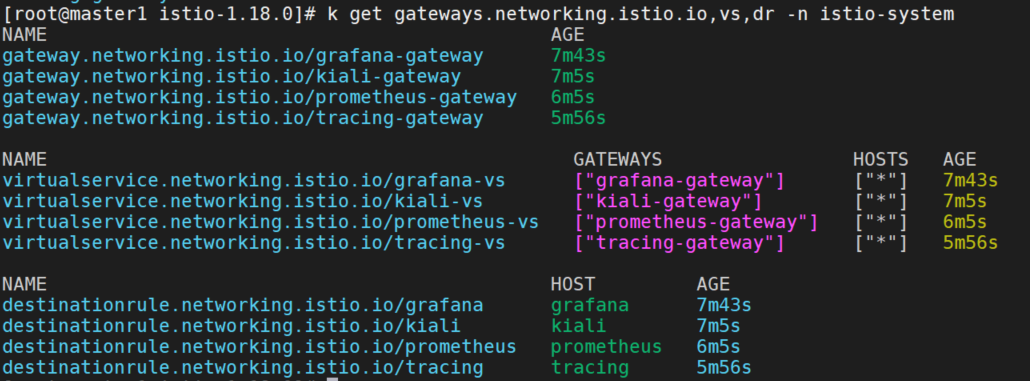
访问方式:
Kiali: http://<IP ADDRESS OF CLUSTER INGRESS>:15029/
Prometheus: http://<IP ADDRESS OF CLUSTER INGRESS>:15030/
Grafana: http://<IP ADDRESS OF CLUSTER INGRESS>:15031/
Tracing: http://<IP ADDRESS OF CLUSTER INGRESS>:15032/但是这样是无法直接访问的,因为我这里没有LoadBalancer。如果想访问需要修改istio-ingressgateway的svc。
k edit svc -n istio-system istio-ingressgateway
# 添加下面的gateway端口
- name: tracing
nodePort: 30032
port: 15032
protocol: TCP
targetPort: 15032
- name: grafana
nodePort: 30031
port: 15031
protocol: TCP
targetPort: 15031
- name: prometheus
nodePort: 30030
port: 15030
protocol: TCP
targetPort: 15030
- name: kiali
nodePort: 30029
port: 15029
protocol: TCP
targetPort: 15029新的访问方式:
Kiali: http://<IP ADDRESS OF CLUSTER INGRESS>:30029/
Prometheus: http://<IP ADDRESS OF CLUSTER INGRESS>:30030/
Grafana: http://<IP ADDRESS OF CLUSTER INGRESS>:30031/
Tracing: http://<IP ADDRESS OF CLUSTER INGRESS>:30032/查看graph
使用bookinfo服务访问测试,再次查看graph。

这个图表示一段时间内流过服务网格的流量。该图使用 Istio 遥测而生成。
要查看度量标准摘要,请选择图中的任何节点或边,以便在右侧的 summary details 面板中显示其度量的详细信息。
要使用不同的图形类型查看服务网格,请从 Graph Type 下拉菜单中选择一种图形类型。有几种图形类型可供选择:App、Versioned App、Workload、Service。
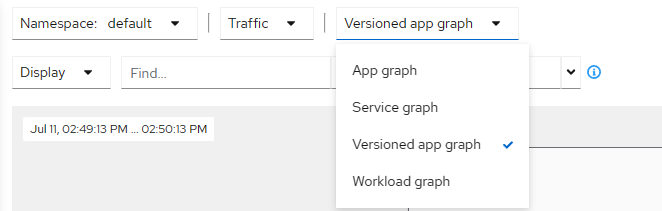
检查 Istio 配置
要检查有关 Istio 配置的详细信息,请点击左侧菜单栏上的 Applications、Workloads 和 Services 菜单图标。

流量转移
可以使用 Kiali 流量转移向导来定义特定百分比的请求流量以路由到两个或多个工作负载。
查看 bookinfo 图的 Versioned app graph。
- 确保已启用 Traffic Distribution Edge Label 的 Display 选项,以查看路由到每个工作负载的流量百分比。
- 确保已经已启用 Show Service Nodes 的 Display 选项,以在图中查看服务节点。
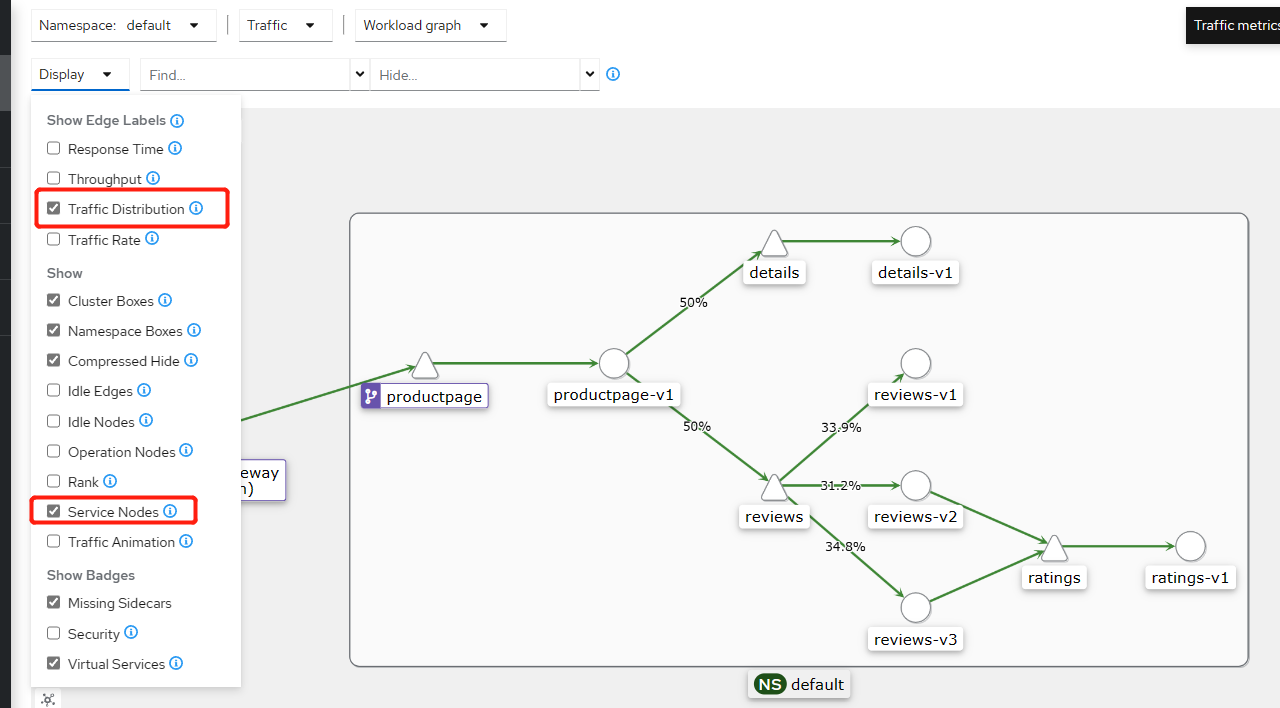
通过点击 reviews 服务 (三角形) 节点,将关注点放在 bookinfo 图内的 reviews 服务上。 注意,reviews 服务流量平均分配给三个 reviews 服务 v1 和 v2 和 v3(每台服务被路由 33.3% 的请求)。
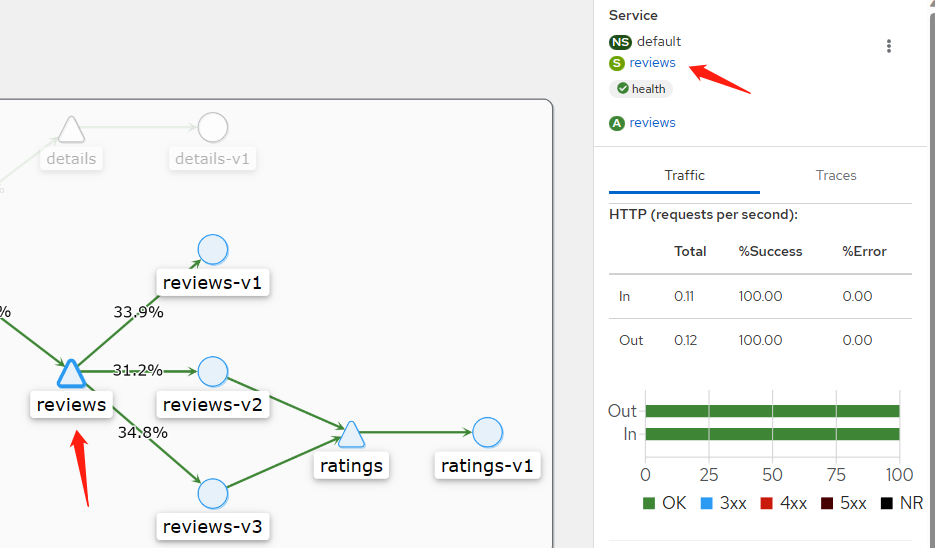
点击侧面板上的 reviews 链接进入 reviews 服务的详情视图。这也可以通过右键点击 reviews 服务节点并从上下文菜单中选择 Details 来完成。

从 Action 下拉菜单中,选择 Traffic Shifting 以流量转移向导。
拖动滑块以指定要路由到每个服务的流量百分比。 对于 reviews-v1,将其设置为 10%;对于 reviews-v2 ,请将其设置为 20%;对于 reviews-v3,将其设置为 70%。
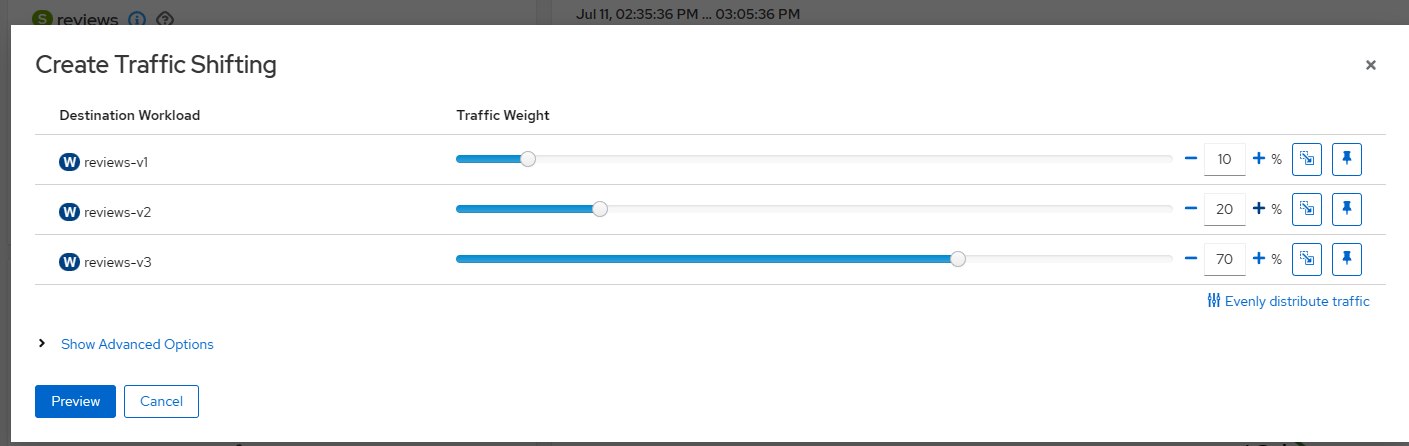
点击 Preview 按钮以查看将由向导生成的 YAML。
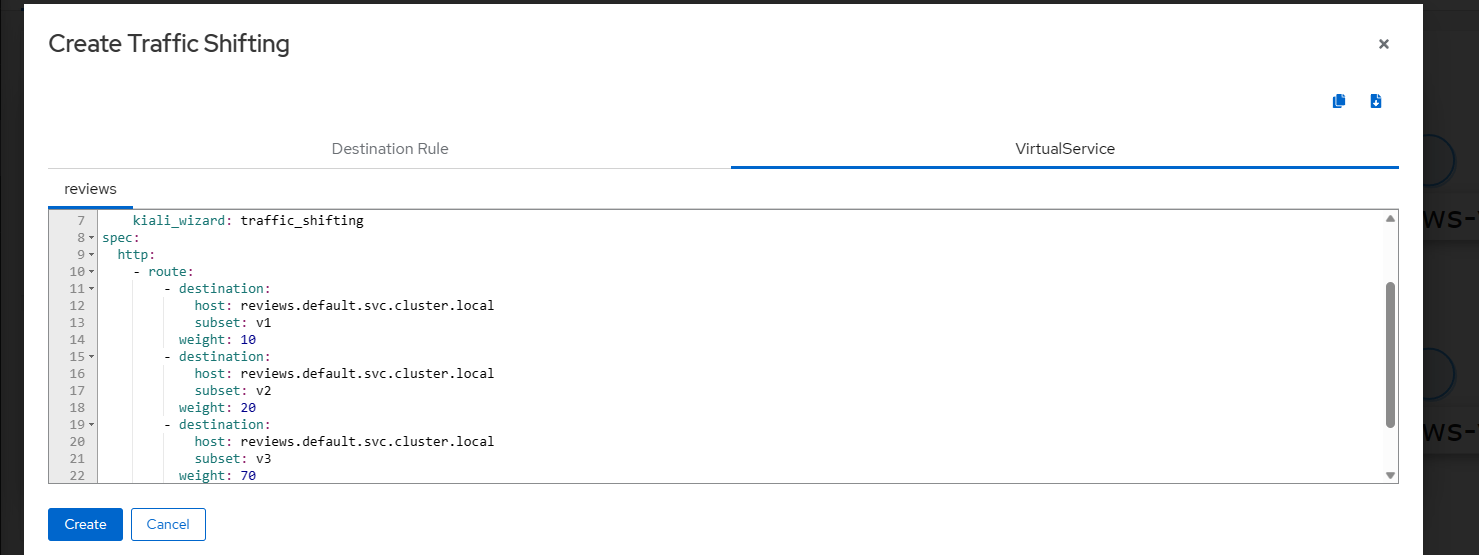
点击 Create 按钮以确认应用新的流量设置。
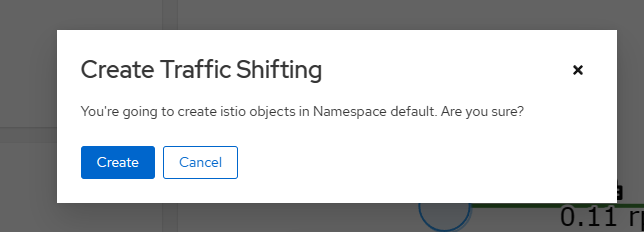
点击左侧导航栏中的 Graph 以返回到 bookinfo 图表。注意现在 reviews 服务节点带有 virtual service 图标。
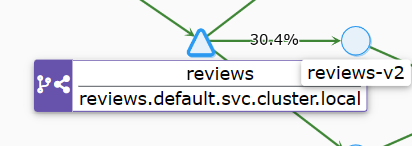
测试访问,流量大致符合比例。

验证 Istio 配置
Kiali 可以验证您的 Istio 资源,以确保它们遵循正确的约定和语义。根据错误配置的严重程度,在 Istio 资源的配置中检测到的任何问题都可以标记为错误或警告。
Istio 提供了 istioctl analyze,它使您能够以在 CI 管道中使用的方式执行类似的分析。这两种方法可以互为补充。
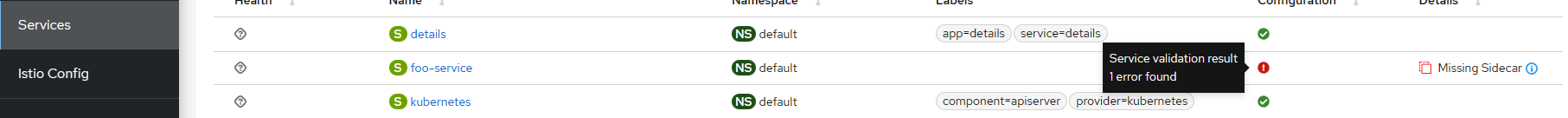
点击 Name 列中的 details 链接,将鼠标悬停在错误图标上可以显示描述错误的提示。
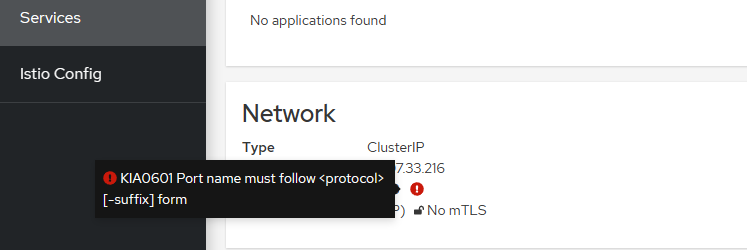
查看并编辑 Istio YAML 文件配置
Kiali 提供了一个 YAML 编辑器,用于查看和编辑 Istio 配置资源。当检测到错误的配置时,YAML 编辑器还将提供验证消息。

在 bookinfo VirtualService 中引入一个错误。
kubectl patch vs bookinfo --type json -p '[{"op":"replace","path":"/spec/gateways/0", "value":"bookinfo-gateway-invalid"}]'
返回kiali可以看到页面报错了:
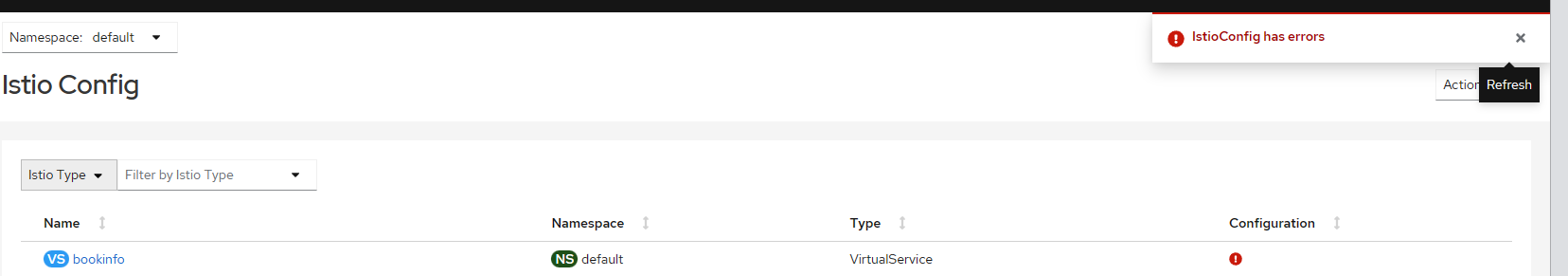
查看报错详细信息:

有关错误起因和解决方法的更多详细信息:https://kiali.io/docs/features/validations/
还原
kubectl patch vs bookinfo --type json -p '[{"op":"replace","path":"/spec/gateways/0", "value":"bookinfo-gateway"}]'集成Jaeger
Kiali 为分布式跟踪提供了与 Jaeger 的本地集成。因此,用户可以访问 Jaeger 的跟踪可视化。但更重要的是,Kiali 将跟踪整合到多个相关视图中,使您在跟踪数据方面的投资更有价值。
工作负载详细信息
调查工作负载时,单击跟踪选项卡以在图表中可视化跟踪。选择跟踪时,Kiali 会显示一个用于跟踪详细信息的选项卡和一个用于跨度详细信息的选项卡。Kiali 总是尝试显示问题区域,Kiali 使用热图方法来帮助用户识别问题痕迹或跨度。
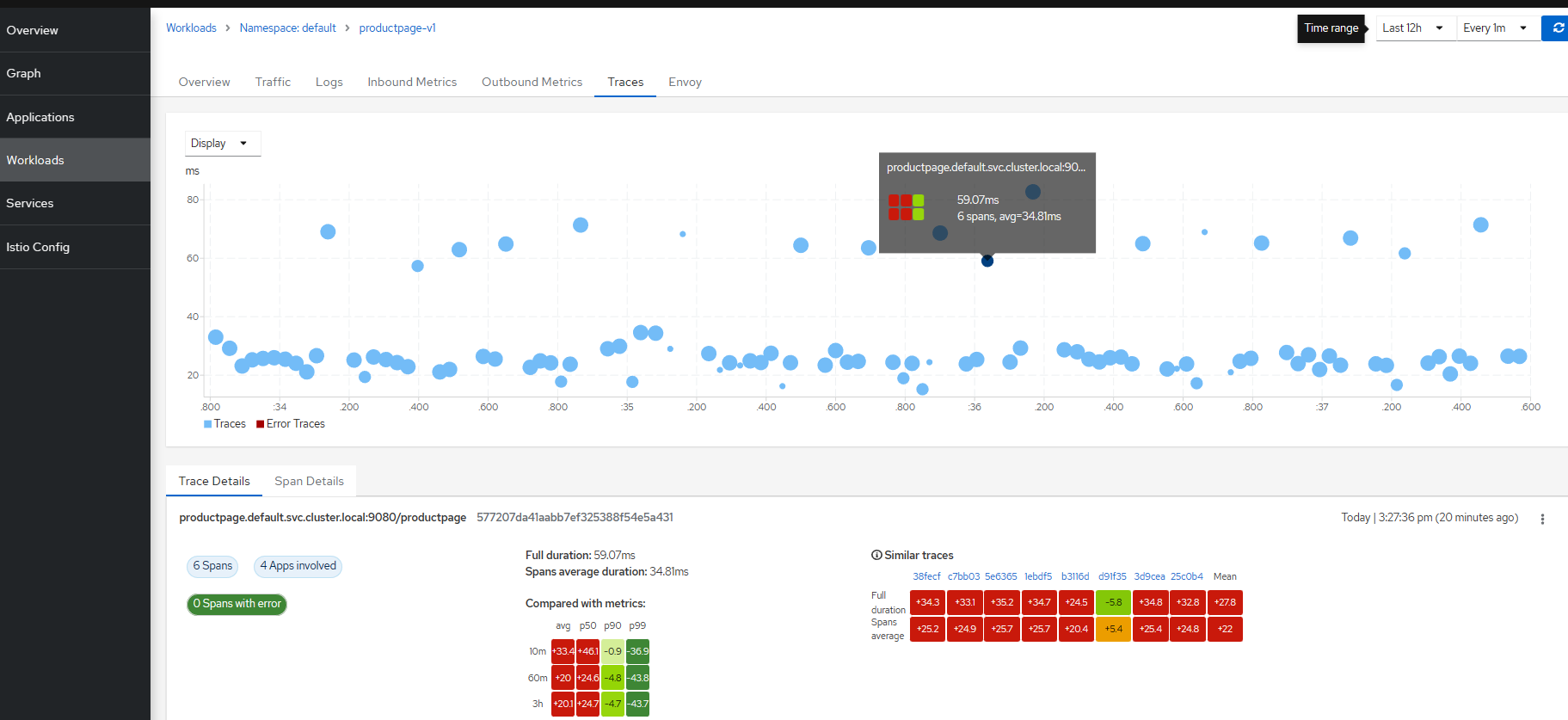

Heatmaps 热图
您在工作负载的“跟踪”选项卡中看到的热图是一个矩阵,用于将特定跟踪的请求持续时间与随时间聚合的持续时间指标进行比较。
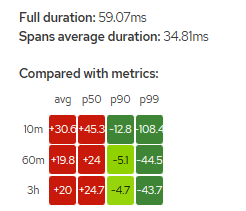
每条跟踪都有一个相应的热图矩阵。矩阵中的每个单元格对应于一个特定的指标聚合;单元格的值和颜色表示该指标与矩阵关联跟踪的持续时间之间的差异。
例如,上面热图的右上角单元格显示,跟踪表示的请求持续时间 (59.07ms) 比过去 10 分钟内所有入站工作负载请求的第 99 个百分位数快 108.4 毫秒。
单元格的颜色范围在红色和绿色之间;单元格越绿,跟踪的持续时间与聚合指标数据的比较速度就越快。红色单元格表示与聚合指标数据相比,关联的跟踪速度要慢得多,因此检查该跟踪有助于检测潜在的瓶颈或问题。
指标相关性
Kiali 在指标图表上提供跨度叠加。用户只需启用该 spans 选项即可生成叠加层。单击任何范围将导航回“跟踪”选项卡,重点关注感兴趣的跟踪。
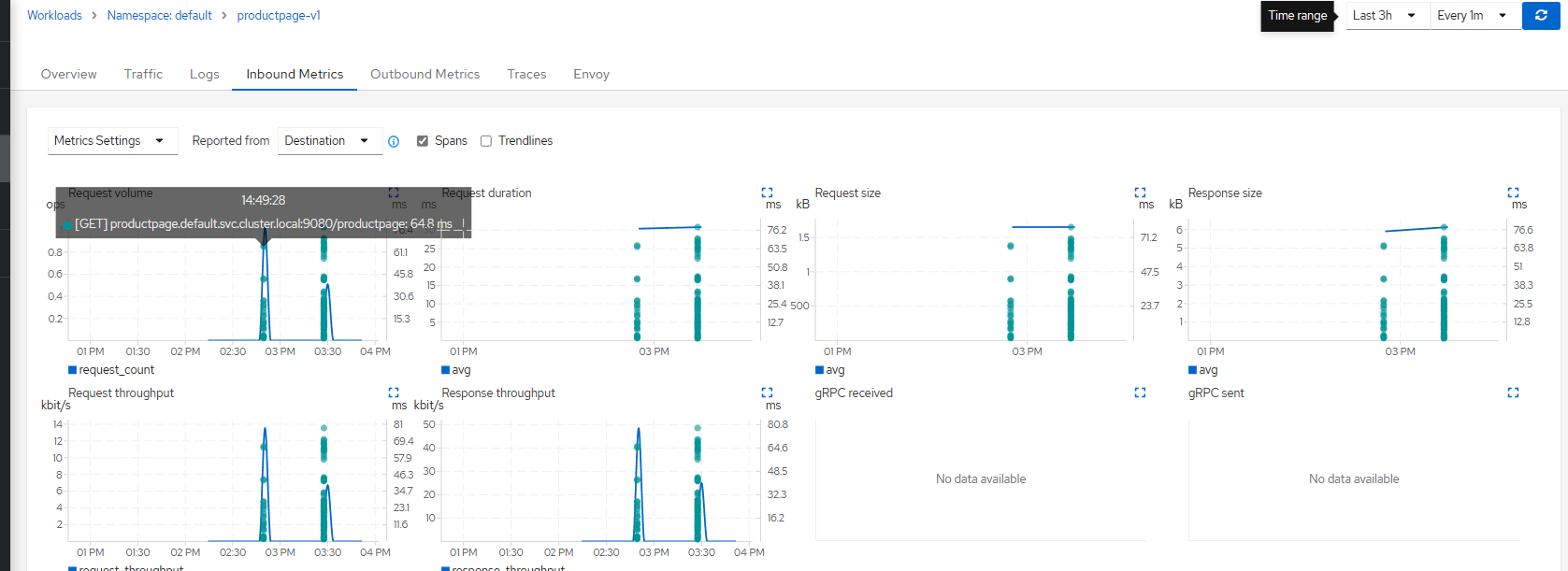
图形相关性
Kiali用户经常使用图形功能来可视化他们的网状流量。在侧面板中,选择图形节点时,用户将看到“跟踪”选项卡,其中列出了该时间段的可用跟踪。选择跟踪时,图形将显示跟踪跨度的叠加层。侧面板将显示跨度详细信息,并提供返回到跟踪详细信息视图的链接。

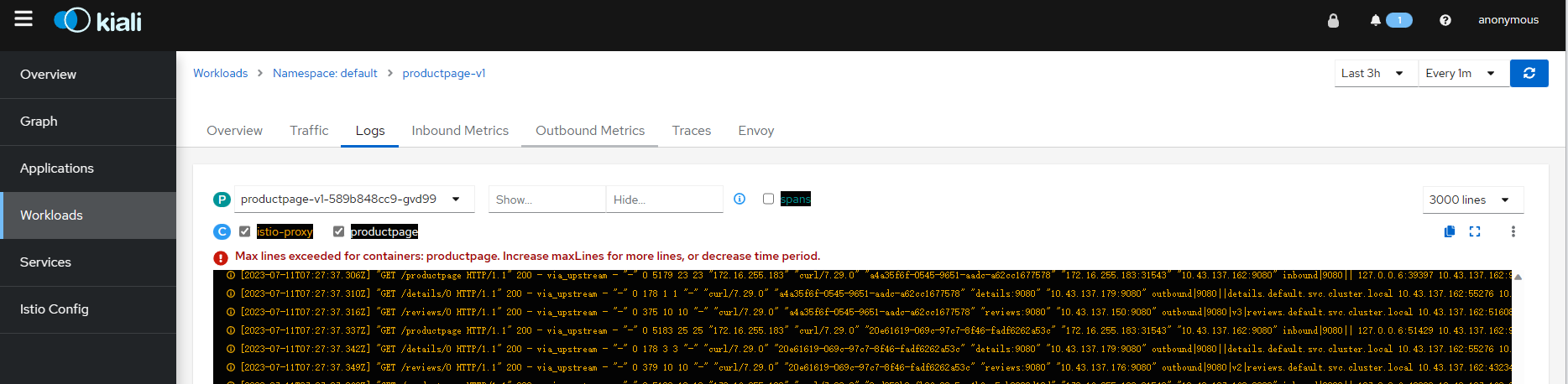
日志关联
Kiali 致力于关联可观测性的标准支柱:跟踪、指标和日志。Kiali 可以呈现日志和跟踪信息的统一视图,这样用户就可以使用日志来识别感兴趣的跟踪。启用选项时, spans Kiali 会将跟踪条目添加到工作负载日志视图。下面,按时间排序顺序,向用户显示应用程序日志(白色)、Envoy 代理日志(金色)和跟踪空间(蓝色)的统一视图。单击感兴趣范围将转到感兴趣跟踪的详细信息视图。